01.
Define a credible and executable IT security roadmap to secure the organization and mitigate the exposed risks.
Get to know our comprehensive Cybersecurity Portfolio: Learn More
Fully managed IT solutions to take your Private Equity portfolio companies to the next level.
Learn MoreAssess critical IT functions for a 360-degree overview of IT costs, risks, value creation opportunities, and an accurate Total Cost of Ownership (TCO) understanding!
Learn MoreOvercome integration challenges after M&A with dedicated IT support that brings together systems, businesses processes, financial infrastructures, and people.
Learn MoreLeverage expert methodologies, experience, and knowledge that has powered thousands of financial transactions, mitigating risks at every carve-out stage.
Learn MoreCreating business value by protecting critical IT systems through entire data lifecycles.
Learn MoreFind unchecked security threats that might be harming your business, empowering your IT infrastructure towards a robust defence framework.
Learn MoreSecuring critical infrastructure by identifying real-world vulnerabilities before attackers do.
Learn MoreGet past typical cybersecurity roadblocks, protecting critical organizational data and aligning your cybersecurity with strategic goals with a tangible implementation roadmap!
Learn MoreStrengthen your IT security defences with industry-leading technology and expertise that protects your assets and meets even the most challenging 24/7 monitoring demands.
Learn MoreOur complete service portfolio for Compliance services from Assessment to Remediation and Monitoring. Our Team will keep your organization in line with your selected framework.
Learn MoreObtain a clear and actionable current state of your organization's audit readiness for SOC 2, ISO 27001 and UK Cyber Essentials.
Learn MoreDevelop a short and long term strategy-level plan for remediating your organization people, processess and tools to obtain a sustainable certification in the shortest time possible.
Learn MoreOur Team's offering that covers our award winning compliance Automation Platform, Consulting, remediation and complete Audit Certification Services.
Learn MoreGet access to a full-service suite offering that maximizes collaboration between teams, delivers best service guidance, and improves the ROI of your cloud licensing investment.
Learn MoreFind unchecked security threats and discover the true maturity and utilization state of your Microsoft 365 environment.
Learn MoreDevelop a long-term strategy-level plan for Microsoft 365 initiatives, establishing a clear blueprint of how internal company processes and your tenant implementation should be improved.
Learn MoreFuture-proof your enterprise on the cloud and streamline your collaboration and security by fully optimizing the utilization of each Microsoft 365 Suite component.
Learn MoreOptimize your Azure implementation and operations, reduce your operational expenses, and improve your end customer experience with managed IT services for your Azure infrastructure.
Learn MoreGain comprehensive understanding of the current state of your Azure environment, identify infrastructure gaps, scope for process risks, and align your tech with business outcomes.
Learn MoreDriving business growth by aligning cloud strategy with your goals through expert-led Azure migration assessments.
Learn MoreDevelop a long-term strategy-level plan for Azure initiatives, having a clear blueprint of how internal company processes and systems will be affected.
Learn MoreShift your focus to higher-level business activities by reducing operational burdens, building sustainable operational advantages, and boosting overall IT service levels.
Learn MoreConozca nuestro completo portafolio de ciberseguridad: Aprenda más
Soluciones de TI completamente gestionadas para llevar a sus empresas de portafolio de Banca de Inversión al siguiente nivel.
Aprenda másEvalúe funciones críticas de TI para obtener una visión de 360 grados de costos de IT, riesgos, oportunidades de creación de valor y entender con precisión el costo total de propiedad (TCO).
Aprenda másSupere desafíos de integración después de M&A con soporte de TI dedicado que une sistemas, procesos empresariales, infraestructuras financieras y personas.
Aprenda másAproveche metodologías expertas, experiencia y conocimientoque ha impulsado a cientos de transacciones financieras, mitigando riesgos en cada paso de una escisión empresarial.
Aprenda másCree valor protegiendo sistemas de TI críticos a través de todo su ciclo de vida de sus datos.
Aprenda másEncuentre amenazas de seguridad no detectadas que le podrían estar haciendo daño a su empresa, fortaleciendo su infraestructura de TI hacia un robusto marco de referencia en defensa.
Aprenda másSupere obstáculos usuales de ciberseguridad, protegiendo datos organizacionales críticos y alineando su ciberseguridad y metas estratégicas con un plan de ruta tangible.
Aprenda másFortalezca sus defensas de seguridad de TI con tecnologías líderes en la industria y experticia que protege sus activos y satisface las demandas de monitoreo 24/7 más desafiantes.
Aprenda másNuestro completo portafolio de Servicios de Cumplimiento, desde Evaluación hasta Remediación y Monitoreo. Nuestro equipo mantendrá su organización en línea con el marco seleccionado.
Aprenda másObtenga un estado actual claro y accionable de la preparación para auditorías de su organización en SOC 2, ISO 27001 y UK Cyber Essentials, entre otros.
Aprenda másDesarrollamos un plan estratégico a corto y mediano plazo para remediar en su organización: equipo, procesos y herramientas con el fin de obtener una certificación sostenible en el menor tiempo posible.
Aprenda másLa oferta de nuestro equipo que cubre nuestra galardonada plataforma de automatización de cumplimiento, consultoría, remediación y servicios completos de certificación.
Aprenda másProvea experiencias de nube computacional consistentes con Azure Hybrid Cloud Express en sus instalaciones en la nube. Integre ambientes de TI aislados con soluciones integradas de nube computacional.
Aprenda másAproveche la Nube Computacional Híbrida más poderosa para SMEs con un clúster de VMware de tamaño ideal preconfigurado y listo para usar.
Aprenda másObtenga accesos a una suite de servicio completo de Microsoft, que maximiza colaboración entre equipos, entrega la mejor guía de servicio y mejora el ROI de su inversión en la nube computacional.
Aprenda másEncuentre riesgos de seguridad previamente ocultos y descubra la real madurez de su organización en la utilización de los servicios de su tenant.
Aprenda másDesarrollo una estrategia a largo plazo para sus iniciativas de Microsoft 365, estableciento un plan claro de como sus procesos internos y la implementación en su tenant deben ser mejorados
Aprenda másGarantice el futuro de su organización en la nube y haga más eficiente su colaboración y seguridad, optimizando la utilización de cada servicio de la suite de Microsoft 365.
Aprenda másProvea experiencias de nube computacional consistentes con Azure Hybrid Cloud Express en sus instalaciones en la nube. Integre ambientes de TI aislados con soluciones integradas de nube computacional.
Aprenda másAproveche la Nube Computacional Híbrida más poderosa para SMEs con un clúster de VMware de tamaño ideal preconfigurado y listo para usar.
Aprenda másOptimice su operación e implementación de Azure, reduzca sus costos operacionales y mejore la experiencia de sus usuarios finales con servicios gestionados de IT para su infraestructura Azure.
Aprenda másObtenga un entendimiento completo del estado actual de su entorno Azure, identifique vacíos de infraestructura, determine el alcance de los riesgos y alinee su tecnología con los resultados de su negocio.
Aprenda másDesarrollo una estrategia a largo plazo para sus iniciativas de Azure, obteniendo un plan claro de como sus procesos y sistemas seran impactados.
Aprenda másFocalice su atención en actividades de negocio de alto nivel, reduciendo sus cargas operacionales, construyendo ventajas operativas sostenibles y dándole un empuje a sus niveles globales de servicios de TI.
Aprenda másGet past typical cybersecurity roadblocks, protect critical organizational data, and align your cybersecurity with strategic goals with a tangible implementation IT roadmap for cybersecurity! Our full IT security strategy roadmap and cybersecurity program roadmap can help get you on your way.
While you may have an IT Security Assessment in place, you need to execute and follow-up across company silos to mitigate security risks and vulnerabilities. You may wonder “how do I create a cybersecurity strategy roadmap?” And that's where we come in!
Cybersecurity concerns have a lot to do with it. And this can be just the tip of the iceberg! If not integrated right, M&As can expose organizations to risks related to Intellectual Property, Litigation, Warranties, and even Taxes. We keep you on track by minimizing distractions and aligning entire IT ecosystems!
*As reported by the Wall Street Journal
CS Lighthouse TRACK service is a part of our Cybersecurity Certification Roadmap Service suite. Our end-to-end engagement path of cybersecurity optimization comprises three service pillars:
Scoping the current cybersecurity ecosystem to pinpoint areas of improvement, process gaps, cybersecurity risks, and misaligned business outcomes.
Laying down a cybersecurity strategy roadmap for a medium to long-term cybersecurity plan that charts out the entire end-to-end cybersecurity path along with internal company processes and systems. This is a cybersecurity roadmap for 2022 and beyond.
Taking over day-to-day cybersecurity operations and management needs before they turn into process material bottlenecks or interfere with business sustainability, security, and scaling or capacity.
Define a credible and executable IT security roadmap to secure the organization and mitigate the exposed risks.
Prioritize the low investment and high reward activities that could improve your overall organization security score
Executive relevant strategies in the least amount of time and within a minimal budget.
Coordinate and communicate the security policies and procedures across the enterprise
Obtain leadership alignment on cybersecurity risk mitigation and budget execution
Attain the necessary level to tap into our CS Lighthouse MANAGE Managed Cybersecurity services.
Finally, the documents are presented to the executive leadership team to deliver a birds-eye view of their organization's IT stance. Directors of IT, CFO or other organizational leaders may utilize the spreadsheet to track control-by-control implementation and use it as a working document.
After establishing a baseline assessment with our Cybersecurity Lighthouse Detect service, we define, navigate and make progress with quarterly follow-ups. Far more than a standard cybersecurity roadmap template, yy leveraging the NIST Cybersecurity Framework, we define a staggered approach to mitigate the highest risk elements that could have a tangible effect on business outcomes.
We align and budget security risks and business expectations with internal IT and management teams to formulate an action plan with consensus and accountability.
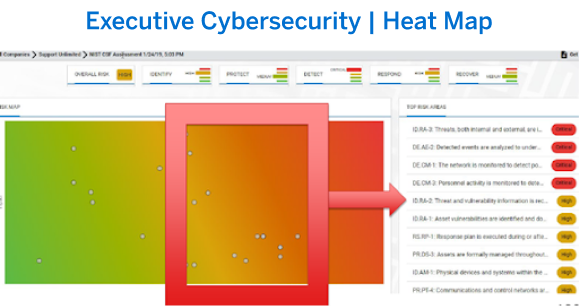
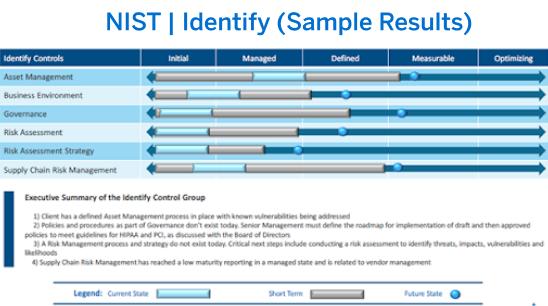
We can help you to create a NIST cybersecurity framework roadmap that can help you with a cybersecurity certification for your organization
Host discovery and mapping of networks, scanning infrastructures, mapping critical systems, and more.
Identifying and scanning for any existing vulnerabilities and possible attacks on the basis of the accrued information.
Password guessing, penetration testing, active exploitation, vulnerability analysis, and more to reveal the true scope of threats.
Identification of areas of improvement and the most prominent risks posed in the process to create an ideal plan of action with the requisite remediation steps.
NIST Cybersecurity findings and recommendations with current, short-term, and future state analysis
Prioritization of scope taking into account both risk level and budget to immediately assess the lowest risk/investment and highest reward actionables.
2-year actionable Cybersecurity Roadmap with quarterly specific work plans and implementation paths.
Access to IT and business leadership with dedicated support
Quarterly follow-up of cybersecurity projects with both internal and external actors
Finally, the documents are presented to the executive leadership team to deliver a birds-eye view of their organization's IT stance. Directors of IT, CFO or other organizational leaders may utilize the spreadsheet to track control-by-control implementation and use it as a working document.
Download Hybrid Cloud Datasheet
Hunters Specialties, is a custom manufacturer and distributor of hunters’ camouflage products, scent products as well as deer and turkey call products...
View MorePaperSource, headquartered in Chicago, Illinois, is a premier Paperie, stationery, and gift retailer that offers papers, custom invitations, and announcements, gifts...
View MoreClockSpring|NRI is a Houston-based provider of high-performance products, engineering support, and training services for critical infrastructure construction and...
View MoreReady To Learn More About Our Private Equity IT Domain Expertise?
With the rich experience of executing dozens of cybersecurity projects from ideation to remediation, we help you leave the firefighter mode behind. Our goal is to make you look beyond the latest threat and adopt a more proactive approach to cyber-attacks.
Have a clear blueprint of the investments that you want to make in people, technology, and processes in order to reach the ideal level of control and security.
Evaluate your tech environment from head to toe to recognize identity and access management woes.
Optimize your entire cybersecurity perspective with a plan that showcases where you stand and what exactly needs to be done to achieve your targets.
Finally, the documents are presented to the executive leadership team to deliver a birds-eye view of their organization's IT stance. Directors of IT, CFO or other organizational leaders may utilize the spreadsheet to track control-by-control implementation and use it as a working document.
· How optimized is the current cybersecurity posture of the organization?
· What is the depth of current security gaps and the best action plan to bridge them?
· How to gain the required long-term executive buy-in to achieve cybersecurity success?
· Which security blueprint will best secure all sensitive data, hardware, cloud resources, etc.?
· What security challenges do teams regularly face while implementing new policies or tools?
· Which plan of action can best address all cybersecurity priorities?
Contact Us and We will get back to you soon.
All The Latest Industry and Organizational Updates. Delivered right to your inbox.
We are an IT consultation powerhouse that designs and operates for private equity asset value creation. We run secure, IT mission-critical workloads for Hybrid Cloud with expert architects and certified engineers in Microsoft Azure Cloud and IBM Cloud.
Get in touch for our cybersecurity assessment report, assessment, and optimization services.
All Rights Reserved ne Digital, Inc.® and ne Graphics, Inc.®
Somos una organización de consultoría de TI que diseña y opera para la creación de valor. Manejamos cargas de trabajo críticas para nubes computacionales híbridas con arquitectos expertos e ingenieros certificados en Microsoft Azure e IBM Cloud.
Póngase en contacto y solicite nuestros servicios.
Todos los derechos reservados ne Digital, Inc.® y ne Graphics, Inc.®
Empresa