With the frequency of cyber attacks increasing, it’s clear that organizations need to make protecting company networks and assets a top priority.
The need for digital transformation in keeping up with real-time attempts by hackers to compromise network security has increased the popularity of the zero trust network model. Zero trust security architecture reinforces an organization’s security framework by ensuring users don’t receive unnecessary access to company resources.
What Is Zero Trust Security?
Zero trust eliminates the idea of automatically giving users, devices, or processes the benefit of the doubt regarding access. For example, a business analyst who’s worked at a company for 15 years may have access to various systems, even if no longer required for their job role.
Under a zero-trust security policy, that user would have access only when needed. Once that goes away, so does the access. The zero trust security model focuses on the protection of company assets like:
- Data
- IT Infrastructure
- Company devices
- Business applications
- End-users
- On-premises servers
- Cloud environments
No one receives implicit trust when it comes to access. Protocols are put in place to never trust anyone or any process. The zero trust network access approach relies heavily on robust access management. That means consistently verifying a user’s identity, process, or application.
You review the need to use that resource to handle a workload. If someone logs in remotely through a company VPN, validation protocols like multifactor authentication (MFA) should be in place. That way, you cut down on vulnerabilities around user identity that could lead to incidents like malware getting into your networks.
It’s much harder for malicious actors to access essential company infrastructure when you treat everything as a potential threat. Make it a point to always verify who needs access and for what reason. Following the zero-trust approach decreases the attack surface for hackers, lowering your organization’s risk of data breaches.
Why is Zero Trust Important?
The flaw in granting users or other accounts a limited level of implied trust is that it leaves loopholes for hackers to exploit. For example, a user with unnecessary permissions to apps might have their credentials stolen by a bad actor looking to harm an organization. They could end up leaving ransomware or other harmful malware within your networks. Companies must exercise strict access control and assume no one within an organization is safe.
Another essential aspect of any zero trust solution is the ability to control who gets past various endpoints. Adaptive identity-based solutions help enforce zero trust policies around infrastructure like cloud services and big data centers. Making zero trust the center of your security guidance enables you to lateral movement from hackers if they manage to gain access to your systems or networks.
What Does the Zero Trust Security Model Involve?
Implementing zero trust within an organization involves a wide array of different techniques. At a minimum, the tools you bring into your company should make it possible for your company to:
- Define user access policies based on the identity of users and accounts using technology like MFA
- Keep sensitive data safe by having the ability to find, categorize, and handle data based on risk levels
- Secure applications and devices by placing monitoring and reporting around all endpoints
- Use analytics to monitor user behavior, what’s happening with organizational resources, and how various accounts connect to internal data
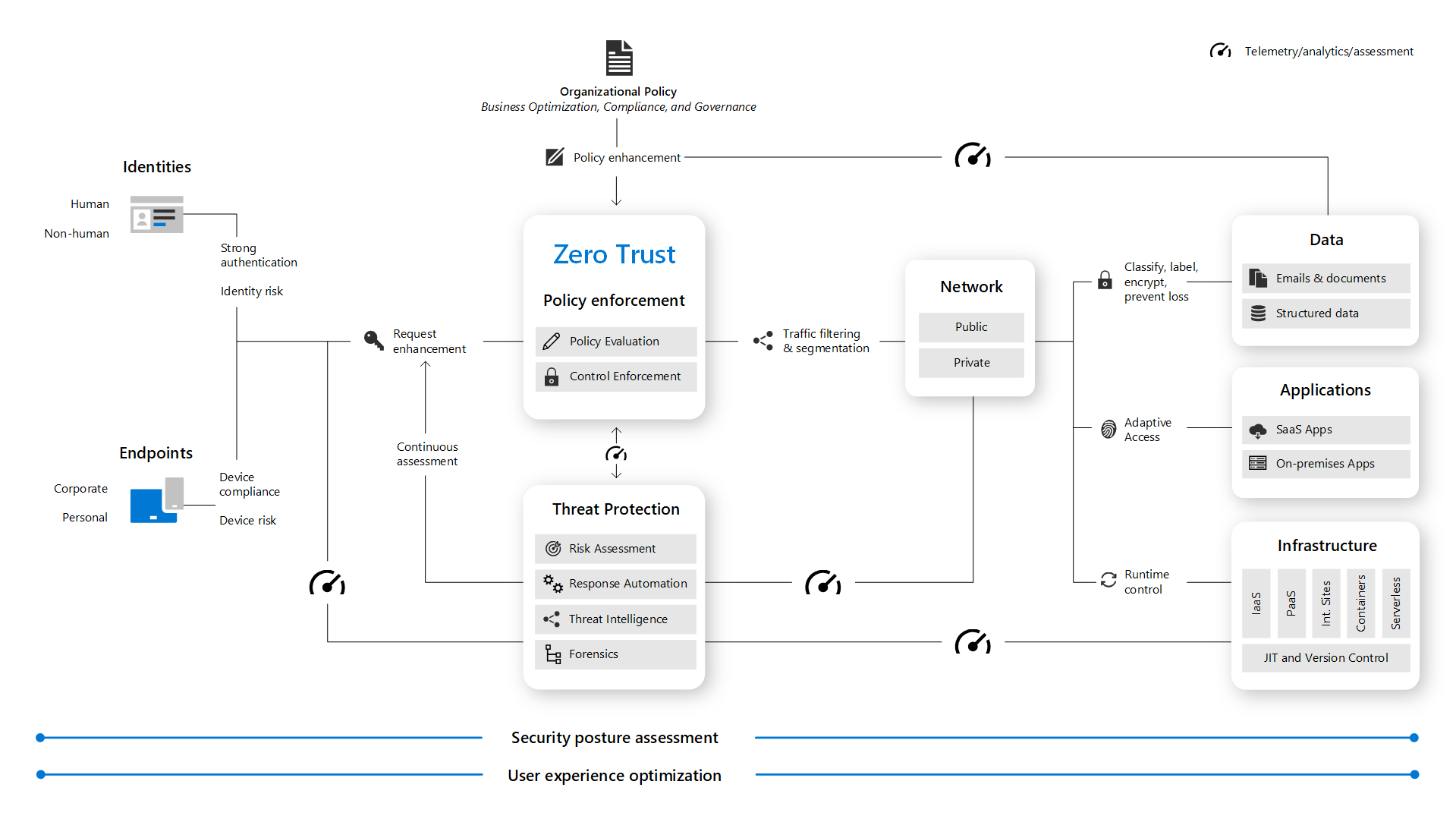
Zero Trust Principles
Zero trust starts with security teams collecting and using information from the entire company. That gives you a clearer understanding of which security strategies to implement. Account for issues like protecting Internet of Things (IoT) technology and ways of mitigating potential threats. Below are the four principles of zero trust that help companies set up governance around how security tools keep assets, data, and resources secure.
1. Define the context
In the past, companies relied heavily on network perimeter security tools to keep intruders out. However, the complexity of emerging technologies like multi-cloud and hybrid network environments decreased the effectiveness of traditional cybersecurity solutions.
With zero trust security, you start by establishing the boundaries of various assets, data, and resources within your company. The process of micro-segmentation helps you figure out what’s most vulnerable to an attack and what criteria to use to determine which users or processes should receive access.
Once you understand your boundaries, determine which tools would work best to conduct regular security inspections and enforce zero trust network access (ZTNA). It’s also important to figure out how to keep hackers from moving around if they manage to gain a foothold within your company infrastructure.
2. Verify access and enforce security
Keep company resources protected by setting up and consistently enforcing zero trust security policies. That includes actively monitoring and validating access requests against the criteria established by your security team. Doing so helps ensure that authorized users quickly receive proper access while bad actors quickly get rejected and tracked. Make the idea of least-privilege access a core part of your security posture.
3. Deal with security incidents
Set up protocols on how to quickly deal with situations where someone manages to get past your firewalls, security controls, and other secure access protections. Examples of use cases around handling breaches include:
- Revoking access from unauthorized users
- Resetting your network components
- Cleaning devices
- Creating and tracking incident tickets
- Generating compliance reports
Your organization should have monitoring in place to detect any malicious or unauthorized activities within your environment. Zero trust architecture should be integrated entirely throughout your corporate security policies and IT infrastructure. Your security team should have what they need to rapidly scale up incident response, perform secure auditing, hunt down threats, and delegate tasks efficiently.
4. Conduct ongoing analysis
You need analytic tools that give you complete visibility into the activities of zero trust security solutions. They help you make more informed decisions around your access policies. Maintaining an effective zero-trust security posture means constantly running analysis tools that monitor, log, connect, and analyze information around security issues across your organization.
How Can You Benefit From Zero Trust Security Architecture?
If you're looking to gain more granular control over the access measures implemented by your organization, it's essential that you make the zero trust model an essential part of your cybersecurity plan. Start by mapping out an action plan on how to revamp critical parts of your security measures to incorporate automated security workflows that enforce zero trust security policies.


